ISU2 Cyber Defense Competition
In this competition we were given a network of computers and were acting as an accounting firm’s IT department. Unfortunately this competition took place the Saturday of mid-terms, so my team did not have much time before the competition to prepare. The first time that we were able to get together as a full team was the Friday night right before the competition. In the prior weeks we knew that we would not have time to prepare thoroughly, and devised a strategy for the competition.
Looking at the point breakdown, keeping all of the flags on the machines being worth only 20% of the overall points that could be earned. With a 50% gain back on the points lost if you can describe how the flags were taken meaning a loss of only 10% of the total points possible. If we were able to do well on the other sections like docs, and anomalies. We could lost those points and have no issues. This led us to come up with the plan of leaving all the default credentials on the machines, since that would allow red team’s automated scripts grab the flags at the competition start. After interactions in prior competitions, we were fully expecting red team to be highly upset about this and try to not give us the points for the flags. So alongside leaving default credentials we setup extremely aggressive logging that would log every command run on the system, and by who. Doing this we were able to capture the logs below showing them logging in, then in the same session planting the flags, and adding their own ssh keys to the machine.
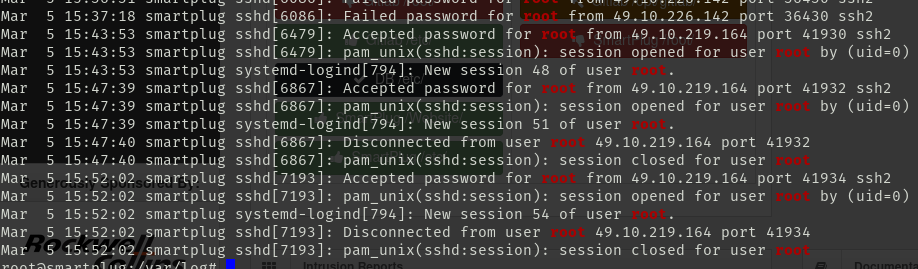
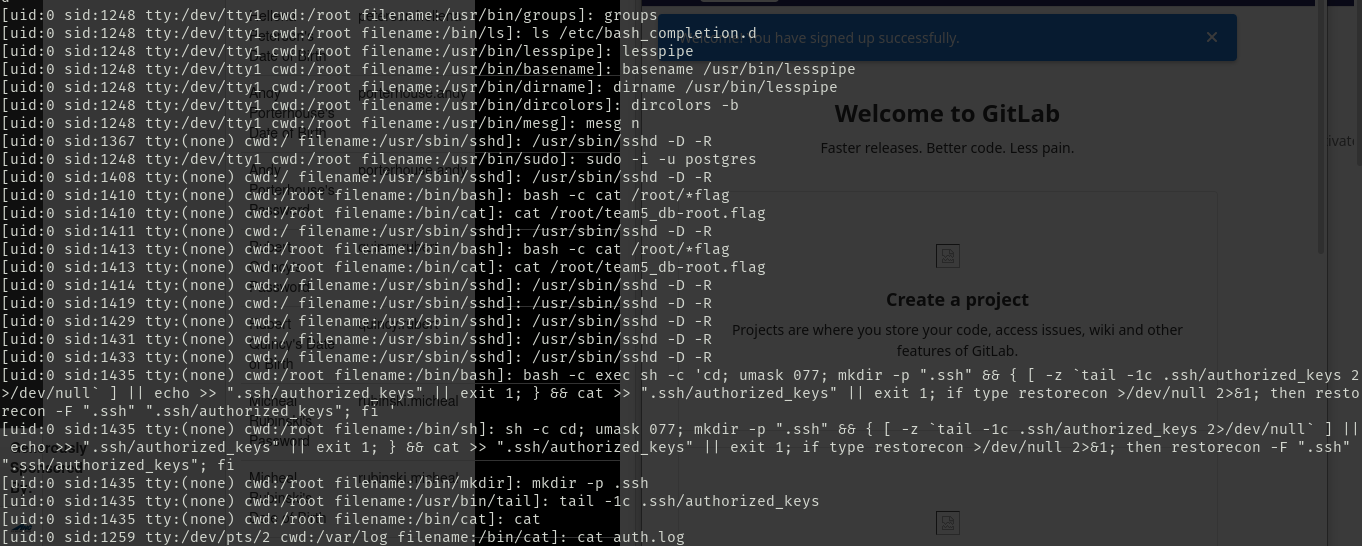
These logs were there to keep red team honest as we were able to find similar logs on every single one of the machines we were given. That was not the only interesting things we found though either. We were able to find red team setting UID bits to root for programs like vim, vi, less, and more. This would give them root access to the machines again if we kicked them out, and they found another non-privileged way into them. Knowing that they were actively doing this, it is something my team is planning on looking out for in the future competitions.
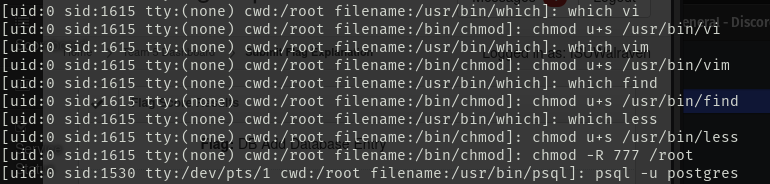
What we did in this competition was very much not the right way of securing our systems, and preventing the red team from getting in. But the strategy we came up with was very effective. After a few hours when most flags had been taken we were in the lead up until the last 15 or so minutes when we slipped into second place. This is where we ended the competition only 17 points (or 1.7% of the total points) short of first place. I also feel like I still gained knowledge in this competition, as it helped me better understand the purpose of good logging, and made me implement it so I know how to do it in the future. It also helped me understand that it is important to know what your most vulnerable piece of software is, as that can help you greatly narrow down the search when looking for an intrusion.
