CYBE230 Lab 11 - Analyzing Log Files
In this lab we took a basic look at Security Event and Incident Management (SEIM), by sending our logs to a Splunk instance, and also having security onion monitoring traffic.
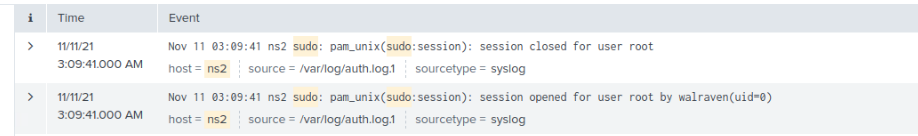
To start off, we pulled the Splunk package and installed it with the basic settings. After creating a login and configuring the receiving settings. We then went to each of the systems we installed the Splunk forwarder to send logs to Splunk. After waiting some time we had the log files delivered to Splunk, and were indexed. To show what a query looks like and what the results look. We were tasked with finding a PAM authentication log of someone using sudo on a system. This is what I found as an example of the logs with sudo being used.
After seeing what a query looked like, we were tasked with finding logs that indicate suspicious activity. One of the first places that I thought to look was the mail server. With only a small amount of mail being sent and received, it would be easy to see suspicious activity in the log. After filtering the logs to only look at the ones from the mail server. I quickly saw that there was a single IP address 88.203.23.50 that was sending a lot of login requests to the server, and was also hitting the default rate limiting.
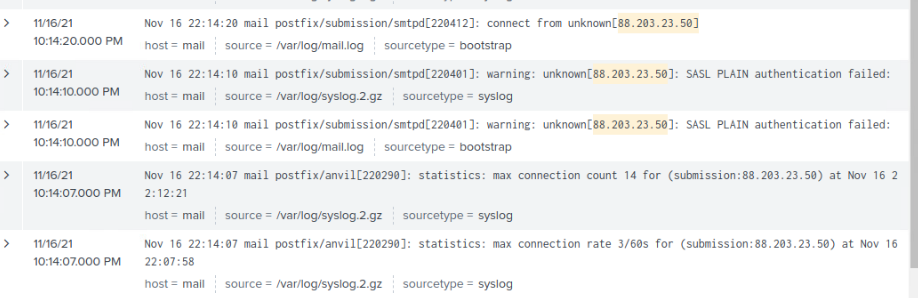
After finding an issue, we asked what some potential options were to deal with this. Unfortunately, part of having a something public facing is that there will be people trying to get into the service. With how often the requests were coming in, and how it was already hitting rate limiting. It might be possible to further restrict the rate limiting. That has the potential to cause more issues though, if this is an IP address used by multiple people, like an apartment building it could be preventing real users from accessing the service.
The next tool we looked at was Security Onion. This monitors and logs network traffic. We set the time frame to traffic from the last day, and had to look for suspicious network activity. When looking through the logs, I saw one of “my” IP addresses generating a lot of NMAP traffic. However, this was not an IP address I was using. It was a rouge address on my network. What I would do is do a physical review and find where the device is, and then remove it from the network.
